Blog.
- #auth0 alternative
- #Authentication
- #custom login
- #API
- #keycloak vs. zitadel
- #auth0 vs. zitadel
- #PHP SDK
- #Ruby SDK
- #Build vs. Buy
- #typescript-login
- #GRPC
- #Python SDK
- #terraform
- #Authorization
- #zitadel
- #announcement
- #Beyond Authentication
- #actions
- #token-management
- #SDK
- #oidc
- #Zitadel SDKs
- #iam
- #multi-tenancy
- #iaac
- #zitadel_cloud
- #community
- #about_us
- #Service Ping
- #Java SDK
- #engineering
- #keycloak alternative
- #how-to
- #features
- #imo
- #open_source
- #pentest
- #security
- #self_hosting
- #case_studies
- #alternative

Full Stack ZITADEL Integration with Next.js
In this tutorial, you'll learn how to set up a Next.js project using JavaScript. You'll also learn how to integrate that with ZITADEL, an open source identity management platform and security layer for your web application.
• 12 min
JWT vs. Opaque Tokens
In this article, you'll learn why you need JWT and opaque tokens, what the differences are between the two, and in which case you should select one or the other.
• 8 min
Why Choose an Open Source Authentication Provider
In this article, you'll learn about open source authentication providers, their common use cases, and what your organization stands to gain from adopting an open source authentication solution.
• 9 min
Security Threats of Public Wi-Fi - Is It Just Fearmongering?
Although public Wi-Fi networks certainly carry some frightening risks with a lot on the line, it is evident that such attacks aren't guaranteed occurrence. So how likely is it really that one will fall victim to a malicious network?
• 9 min
Does your application only support SAML? Fear not, ZITADEL can help you!
With the latest version of ZITADEL we introduced support for the security a session markup language protocol which gives you a broad range of new options for Single-Sign-On with your favorite apps
• 2 min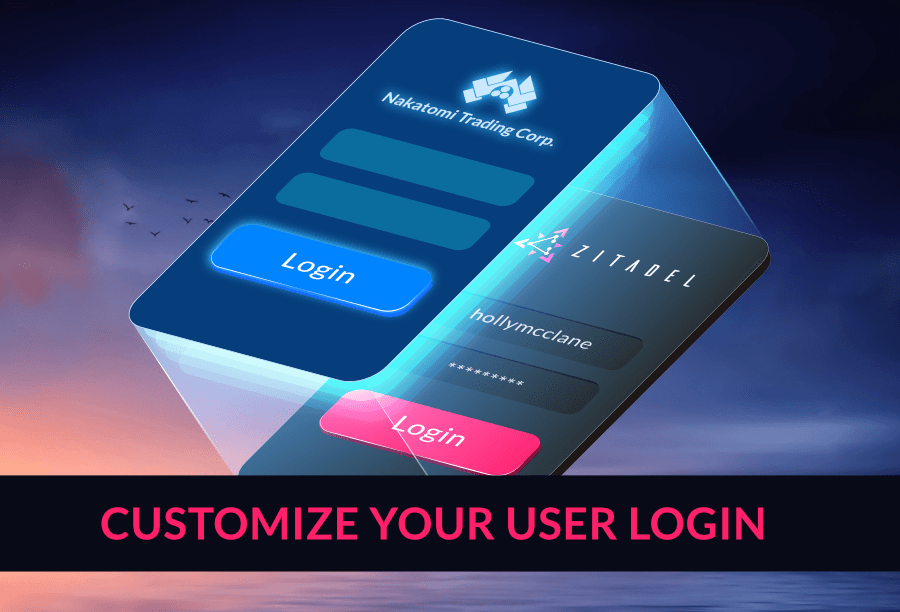
Use OIDC Authorize Request to Customize User Login
One of the critical challenges in designing software systems is identity management. User accounts need to be created, maintained, and promptly secured to ensure the safe and continuous functionality of critical business systems. However, doing so is easier said than done.
• 9 min
You wanted PostgreSQL? We got you covered.
We extend the database compatibility of ZITADEL with support for PostgreSQL databases in addition to CockroachDB.
• 2 min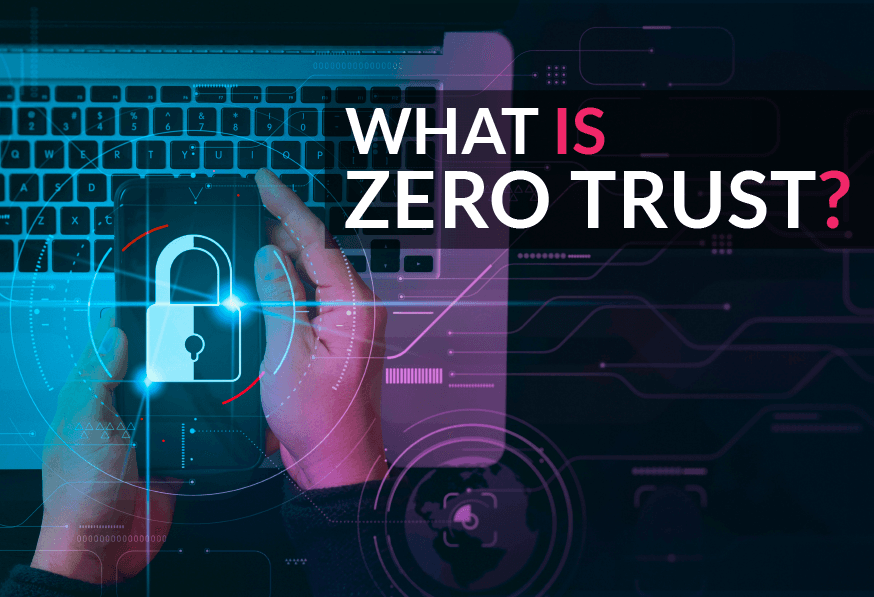
Why Zero Trust is Important
Given the ever-growing prevalence of remote jobs, bring your own device (BYOD), as well as SaaS and cloud-based assets, the importance of secure and trustworthy authentication processes has significantly increased. This article explains the functionality of Zero Trust and its benefits over older security perimeters.
• 5 min
Everything you need to know about Multitenancy
This article discusses multitenancy's definition and its benefits over a single-tenant SaaS architecture.
• 5 min
Introducing ZITADEL Version 2.0!
As a result of many months of diligent effort from our community and developers, we are thrilled to finally announce the first significant upgrade to our Identity & Access Management (IAM) platform - ZITADEL Version 2.0.
• 5 min
Children and Online Security: Protecting the Most Vulnerable
Given a child's natural innocence, they might not expect an ill-wisher on their favourite online platform. This article discusses the new digital threats kids are subjected to and what adults can do to keep them safe.
• 11 min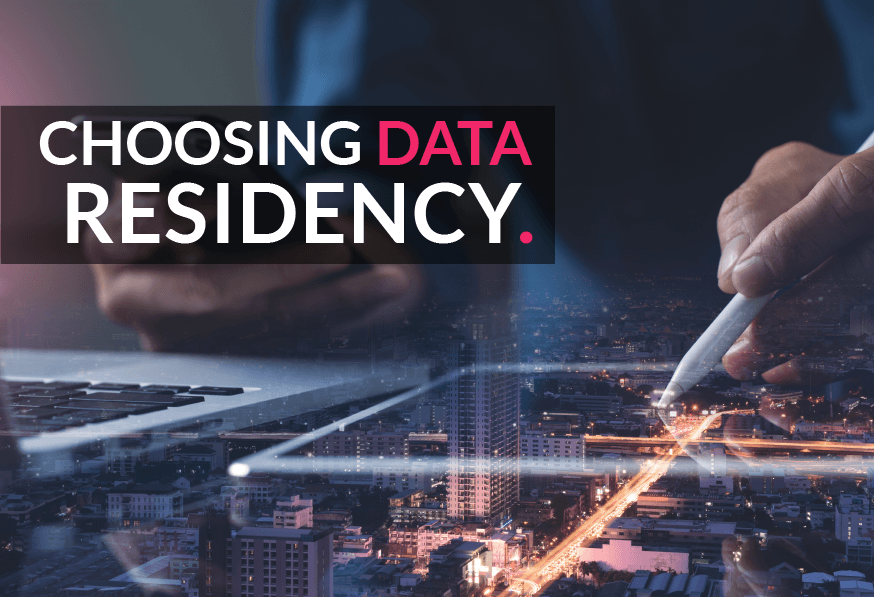
The Ultimate Guide to Choosing the Right Data Residency
This article explains the role of data residency and centers in greater detail and list the factors you might want to consider when choosing a center region.
• 8 min